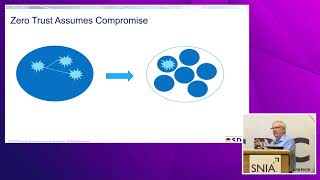
Ransomware attack mitigation has been a high profile problem and is getting more visibility in recent years due to the high payback from victims to have their data released. This proposal implements a series of ‘recognition’ triggers within a layered file system on Windows, which forces a caller through a form of 2FA to potentially reduce the impact of the attack. The approach taken by Thales, within the layered file system implementation for data protection, leverages several layers to recognize when a potential threat is executing. These recognition triggers include the following: - Data variance on access to a given file as compared between cached reads and writes. This would allow a high deviation of the data variance to potentially be recognized as an exploit reading in data content, encrypting it, and writing it back to the file. - A learning mode which would understand data access patterns, on a per file basis, for a given user or for a given set of files. Divergence outside of the norms recorded would potentially recognize a file scan performed by exploits. Of course protecting against a ransomware attack is an ever changing field of play. Approaching a solution from the perspective of reducing impact vs. completely mitigating the exploit, is appealing from both a design and cost perspective. And while a solution which would force a 2-factor authentication pathway would prove to be cumbersome at times for users, it will reduce the impact of potential data loss.
Data Loss Mitigation through 2-Factor Authentication
Wed Sep 14 | 2:30pm
Location:
Salon V
Abstract
Learning Objectives
- Understanding differences between general user data access patterns and those from typical ransomware
- How a typical ransomware exploit obfuscates data
- Data variance comparison algorithms and how to recognize clear vs cipher text
- Incorporating 2FA into a security system without impacting the user ... too much
---
Rajesh Gupta
Thales
Related Sessions